Aim: RC4 Implementation:
- Encryption
- Decryption
Theory :
RC4 was designed by Ron Rivest of RSA Security in 1987; while it is officially termed “Rivest Cipher 4”, the RC acronym is alternatively understood to stand for “Ron’s Code”.
RC4 is a stream cipher, symmetric key algorithm. The same algorithm is used for both encryption and decryption as the data stream is simply XORed with the generated key sequence. The key stream is completely independent of the plaintext used. It uses a variable length key from 1 to 256 bit to initialize a 256‐bit state table. The state table is used for subsequent generation of pseudo‐random bits and then to generate a pseudo‐random stream which is XORed with the plaintext to give the ciphertext.The algorithm can be broken into two stages: initialization, and operation. In the initialization stage the 256‐ bit state table, S is populated, using the key, K as a seed. Once the state table is setup, it continues to be modified in a regular pattern as data is encrypted.
The initialization process can be summarized by the pseudo‐code:
j = 0;
for i = 0 to 255:
S[i] = i;
For i = 0 to 255:
j = (j + S[i] + K[i]) mod 256;
swap S[i] and S[j];
It is important to notice here the swapping of the locations of the numbers 0 to 255 (each of which occurs only once) in the state table. The values of the state table are provided. Once the initialization process is completed, the operation process may be summarized as shown by the pseudo code below:
i = j = 0;
for (k = 0 to N‐1)
{
i = (i + 1) mod 256;
j = (j + S[i]) mod 256;
swap S[i] and S[j];
pr = S[ (S[i] + S[j]) mod 256]
output M[k] XOR pr
}
Where M [0…N‐1] is the input message consisting of N bits. This algorithm produces a stream of pseudo‐random values. The input stream is XORed with these values, bit by bit. The encryption and decryption process is the same as the data stream is simply XORed with the generated key sequence. If it is fed in an encrypted message, it will produce the decrypted message output, and if it is fed in plaintext message, it will produce the encrypted version .
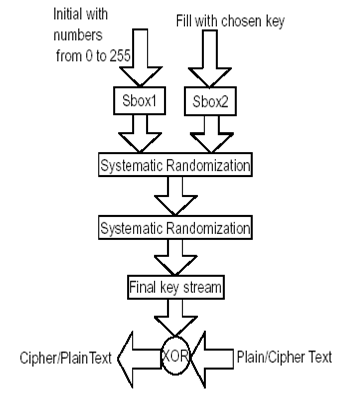
The RC4 encryption algorithm is shown in Fig.
RC4 Steps:
The steps for RC4 encryption algorithm is as follows:
1‐ Get the data to be encrypted and the selected key.
2‐ Create two string arrays.
3‐ Initiate one array with numbers from 0 to 255.
4‐ Fill the other array with the selected key.
5‐ Randomize the first array depending on the array of the key.
6‐ Randomize the first array within itself to generate the final key stream.
7‐ XOR final key stream with the data to be encrypted to give cipher text.
Some of the RC4 algorithm features can be summarized as:
1‐ Symmetric stream cipher
2‐ Variable key length.
3‐ Very quick in software
4‐ Used for secured communications as in the encryption of traffic to and from secure web sites using the SSL protocol.
Algorithm Terminology
RC4 = Ron?s code # 4 or Rivest
Cipher = a cryptographic algorithm used for encryption and decryption.
Symmetric key algorithm = an algorithm that uses the same key to
encrypt and decrypt
Stream cipher = algorithm that encrypts data one byte at a time
Anonymous remailer = distribution system that strips off all of the sender
information and remails the message under an anonymous name.
State table:
It is a table initialized from 1 to 256 bytes. The bytes in the table are used for subsequent generation of Pseudo‐Random bytes. The Pseudo‐Random stream generated is XORed with the plaintext to give the ciphertext.
Source Code:
class RC4Demo
{
String strPlainText;
static char cipher[];
RC4Demo(String strPlainText,int []key)
{
this.strPlainText = strPlainText;
int S[] = new int[255];
cipher = new char[strPlainText.length()];
for (int i=0;i<S.length;i++)
{
S[i] = i;
}
int i=0;
int j=0;
for (int k=0;k < strPlainText.length();k++)
{
int modk = (k%key.length);
int Kc = key[modk];
j = (S[i] + j + Kc) % 256 + 1;
int temp = S[i];
S[i] = S[j];
S[j] = temp;
int Sc = (S[i]+S[j]) % 256;
int Ck = S[Sc];
cipher[k] = (char) (Ck ^ (int)strPlainText.charAt(k));
i = i+1;
}
}
public static void main(String[] args)
{
int K[] = {1, 2, 3, 4, 5};
String strOriginal = “Hello World”;
System.out.println(“Original String‐‐> “+strOriginal);
new RC4Demo(strOriginal,K);
for (int i=0;i<cipher.length;i++)
{ System.out.print(” “+cipher[i]); }
}
}