Aim : implement DES algorithm
Theory :
Encryption Algorithms :
The most commonly used Symmetric Encryption Algorithms are block ciphers. A block ciphers processes the plain text in fixed size blocks and produces a block of cipher text of equal size for plain text block.
The two most important symmetric algorithms, both of which are block ciphers,
are:
• Data Encryption Standard. (DES).
• Advanced Encryption Standard.
Data Encryption Standard :
The DES was officially adopted as U.S federal standard in November, 1976 and authorized by NBS for used on all public and private sectors unclassified communication. DES was accepted as International Standard by International Standard organization. DES algorithm is careful and complex combination of: Substitution and Transposition.
The algorithm derives its strength from the repeated applications of these two techniques one on the top of the other, for a total of 16 cycles. The algorithm begins by encrypting plaintext as a block of 64‐bits. The key is 64‐ bit long, but it can be any 56‐bit number. The extra 8‐bits are often used as check digit. The key can be changed by user security purpose.
In DES algorithm the techniques Substitution provides the Confusion and Transposition provides Diffusion. DES uses only standard arithmetic and logical operations on number up to 64‐bit long. So it can be used in current computers. The algorithm is repetitive, making it suitable for implementation on a single purpose chip.The chip can be used as basic
component in devices that uses DES encryption in application.
Nonce: A value used only once by a computer security system
In security engineering, a nonce is a number used once. It is often a random or pseudo‐random number issued in an authentication protocol to ensure that old communications cannot be reused in replay attacks. For instance, nonces are used in HTTP digest access authentication to calculate an MD5 digest of the password. The nonces are different each time that the 401 authentication challenge response code is presented, and each client request
has a unique sequence number, thus making the replay attack virtually impossible.
Initialization vector (IV)
All these modes (except ECB) require an initialization vector, or IV ‐‐ a sort of ‘dummy block’ to kick off the process for the first real block, and also to provide some randomization for the process. There is no need for the IV to be secret, in most cases, but it is important that it is never reused with the same key. For CBC and CFB, reusing an IV leaks some information about the first block of plaintext, and about any common prefix shared by the two messages. For OFB and CTR, reusing an IV completely destroys security. In CBC mode, the IV must, in addition, be randomly generated at encryption time.
Source Code:
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
import javax.swing.JOptionPane;
public class DES{
public static void main(String[] args) throws Exception {
KeyGenerator keygen = KeyGenerator.getInstance(“DES”);
// create a key
SecretKey secretkey = keygen.generateKey();
Cipher cip = Cipher.getInstance(“DES”);
// initialise cipher to with secret key
cip.init(Cipher.ENCRYPT_MODE, secretkey);
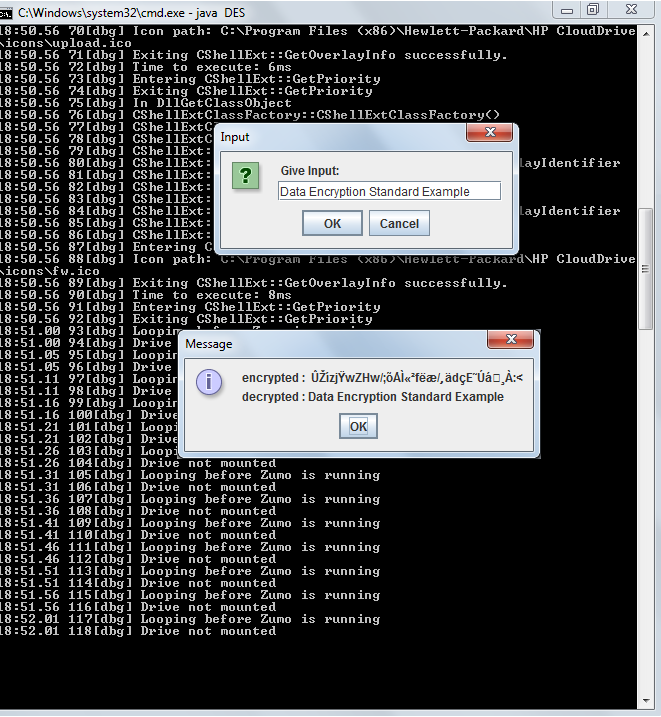
String inputText = JOptionPane.showInputDialog(” Give Input: “);
byte[] encrypted = cip.doFinal(inputText.getBytes());
cip.init(Cipher.DECRYPT_MODE, secretkey);
byte[] decrypted = cip.doFinal(encrypted);
JOptionPane.showMessageDialog(JOptionPane.getRootFrame(),
“encrypted : ” + new String(encrypted) + “\n” +
“decrypted : ” + new String(decrypted));
System.exit(0);
}
}
Output: